An Interesting M365 Billing Scam¶
Update¶
I called the 888 number this morning and it does indeed go to a scam call center. I played along with the person on the other end, who ultimately wanted my first and last name, email address, the order number, and most importantly, my credit card number, so they “could reverse the charge” 🤣
The Scam¶
This is a case where I’d actually love to see how this plays out – when you see the way that scammers try to string things together. I’ve been receiving a rash of unpaid toll bill texts, which give themselves away pretty easily based on the source number. But I’m not here to talk about that scam.
Instead, I’m here to dig into this email I received last week:
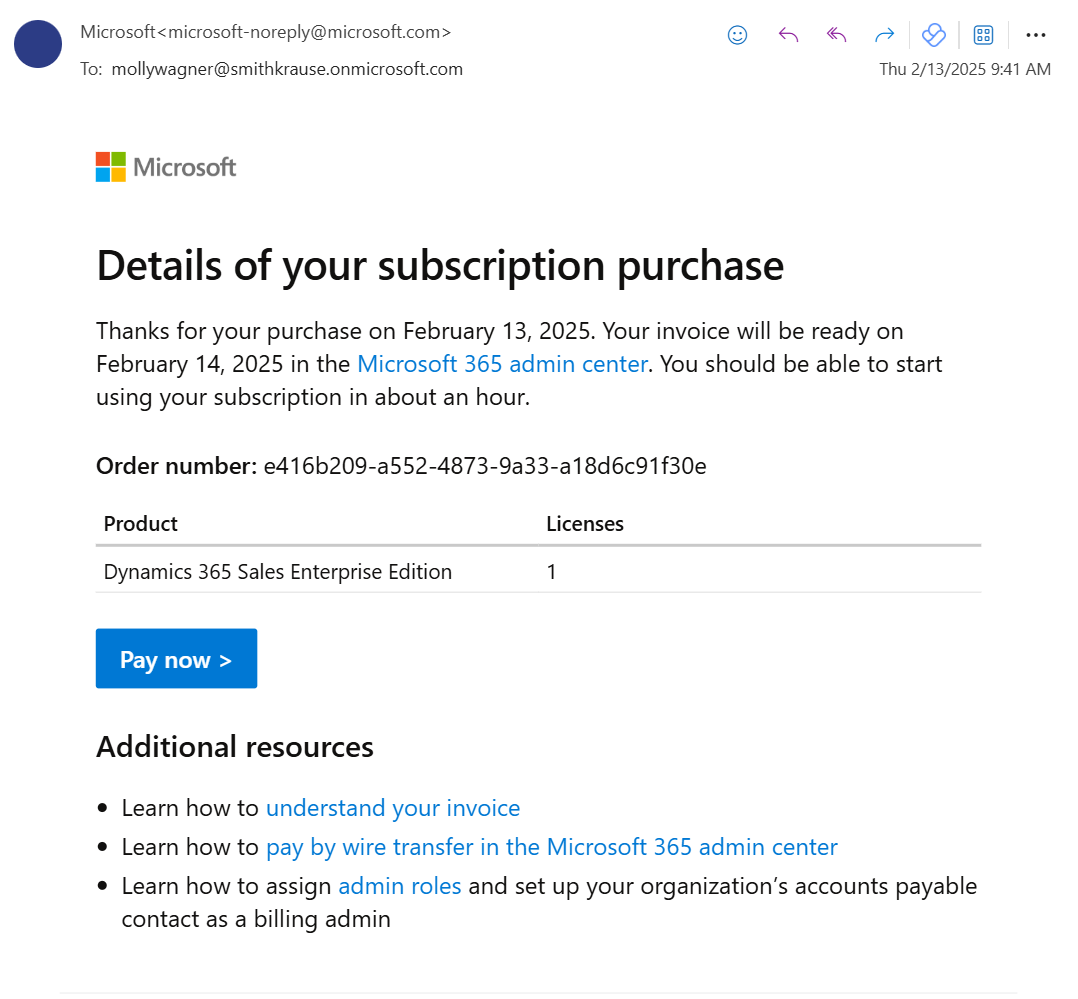
Last time I checked, I’m not Molly Wagner
It looked authentic, and when I checked the headers, it is indeed from Microsoft. I do subscribe to various Microsoft services and receiving emails like this are not abnormal, but I was certainly confused by the service, as well as who it was to.
I scroll down a bit more into the rest of the email:
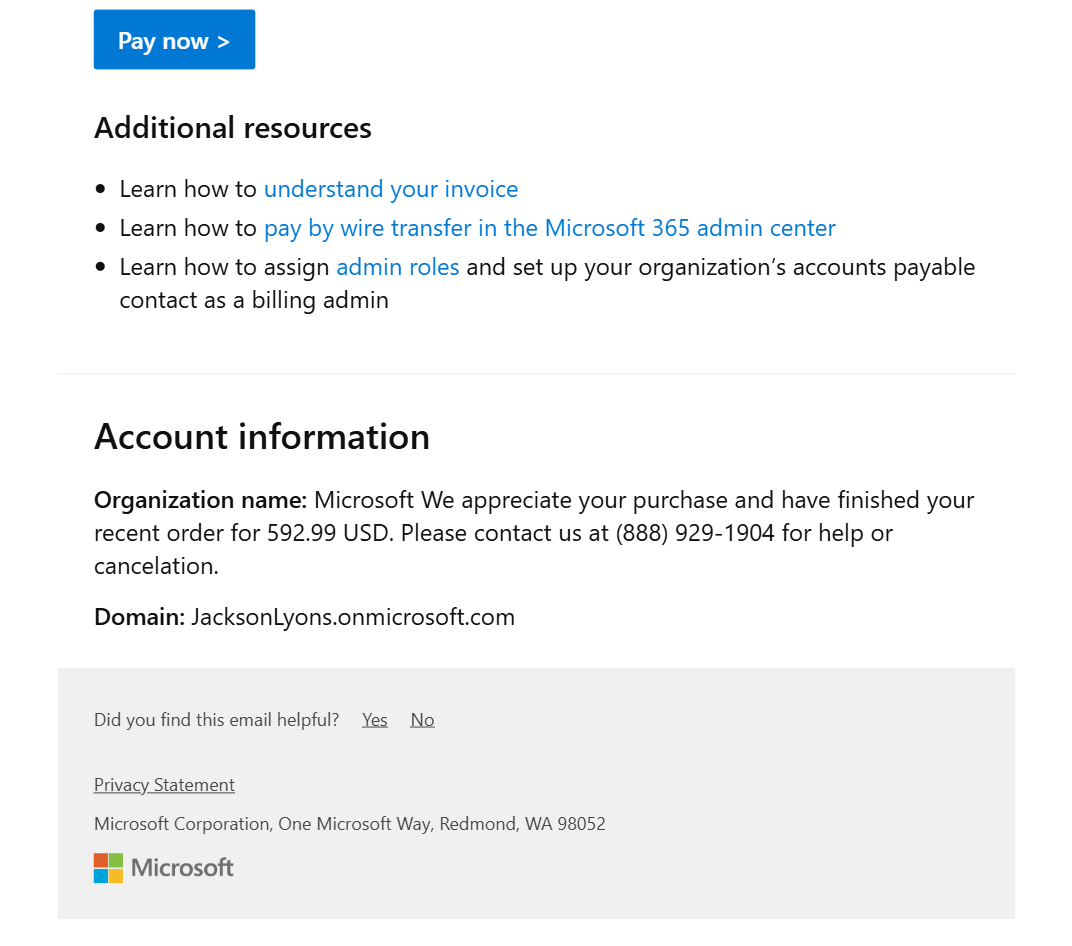
Notice anything unusual? At first, I didn’t. To give myself props, even though it all seemed legitimate, I didn’t click on the link.
But when I saw the domain JacksonLyons.onmicrosoft.com I decided to go look it up over at https://aadinternals.com/osint/. The results:
| Property | Value |
|---|---|
| Default domain | JacksonLyons.onmicrosoft.com |
| Tenant name | null |
| Tenant brand | Microsoft We appreciate your purchase and have finished your recent order for 592.99 USD. Please contact us at (888) 929-1904 for help or cancelation. |
| Tenant id | 6cc54dbc-77fb-44e7-9c6f-ca766a8e26b1 |
| Tenant region | NA |
| Seamless single sign-on (SSSO) | disabled |
| Uses Azure AD Connect cloud sync | N/A |
| Certificate-based authentication (CBA) | N/A |
The results make me wonder if the tenant is turned off on the Microsoft side, as there are no verified domains, but there is a Tenant ID, and the interesting Tenant brand.
Of course, it appears that smithkrause.onmicrosoft.com is the vehicle behind this, and in particular mollywagner@smithkrause.onmicrsoft.com.
Back to another lookup courtesy of @drazuread.bksy.social:
| Property | Value |
|---|---|
| Default domain | SmithKrause.onmicrosoft.com |
| Tenant name | SmithKrause.onmicrosoft.com |
| Tenant brand | SmithKrause |
| Tenant id | eecfe604-36e5-4e7c-86ee-2313e05112aa |
| Tenant region | NA |
| Seamless single sign-on (SSSO) | disabled |
| Uses Azure AD Connect cloud sync | N/A |
| Certificate-based authentication (CBA) | N/A |
| Verified domains | 2 |
| Domain | Type | STS |
|---|---|---|
| addiamaryellen.gigasphere.site | Managed | |
| SmithKrause.onmicrosoft.com | Managed |
Pulling a whois of gigasphere.site, the domain is relatively fresh:
Domain Name: GIGASPHERE.SITE
Registry Domain ID: D524536986-CNIC
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: https://namecheap.com
Updated Date: 2025-02-05T10:49:53.0Z
Creation Date: 2025-02-05T10:49:48.0Z
Registry Expiry Date: 2026-02-05T23:59:59.0Z
Registrar: Namecheap
Registrar IANA ID: 1068
When digging into DNS, both gigasphere.site and addiamaryellen.gigasphere.site only have MX and SPF records for EXO (gigasphere.site DNS is hosted by Cloudflare).
Of course, the email originated from a smithkrause.onmicrosoft.com domain, which I can’t tell the age of, or at least not through AAD Internals OSINIT. Another interesting thing to note is that the people behind the scam are populating a distribution list with the target email addresses; when looking at the headers the To: is indeed mollywagner@smithkrause.onmicrosoft.com.
In due diligence I submitted the email review in M365 Defender, which came back with a no threats found
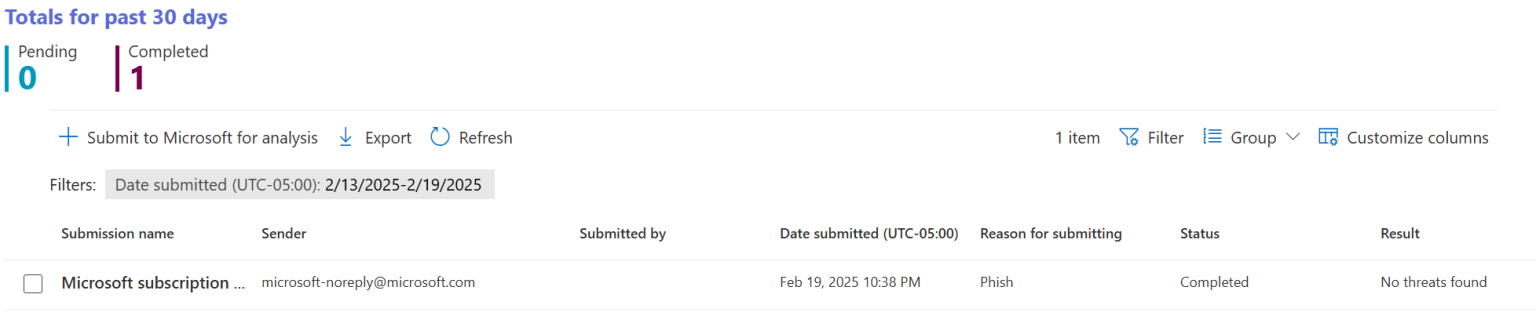
Apparently, the body of the email containing "Microsoft We appreciate your purchase and have finished your recent order for 592.99 USD. Please contact us at (888) 929-1904 for help or cancelation." isn’t sufficient enough to be considered suspicious 🙄.
For fun, I did call the number, but right now the scammers number just forwards to a voicemail box; if I’m able to get ahold of them and resolve my billing issues I’ll follow up 😉.
And the link? The link is benign, it just goes to the M365 admin billing portal, because the email as far as I can tell is legit from Microsoft.
The first few hops on the headers appear to be coming from some MS backend service and it hits the DL on hop 5, based on looking at the headers on https://mxtoolbox.com/EmailHeaders.aspx:
| Hop | Delay | From | By | With | Time (UTC) | Blacklist |
|---|---|---|---|---|---|---|
| 1 | * | outlook.office365.com 2603:10b6:303:18d::16 | MW4PR20MB4527.namprd20.prod.outlook.com | HTTP | 2/13/2025 2:40:06 PM | ✅ |
| 2 | 2 seconds | NAM10-DM6-obe.outbound.protection.outlook.com 2a01:111:f403:2413::720 | SJ1PEPF00002313.mail.protection.outlook.com 2603:10b6:a0f:fc02::1a7 | Microsoft SMTP Server (version=TLS1_3, cipher=TLS_AES_256_GCM_SHA384) | 2/13/2025 2:40:08 PM | ✅ |
| 3 | 0 seconds | SJ1PEPF00002313.namprd03.prod.outlook.com 2603:10b6:a03:54:cafe::b3 | BYAPR02CA0055.outlook.office365.com 2603:10b6:a03:54::32 | Microsoft SMTP Server (version=TLS1_3, cipher=TLS_AES_256_GCM_SHA384) | 2/13/2025 2:40:08 PM | ✅ |
| 4 | 0 seconds | BYAPR02CA0055.namprd02.prod.outlook.com 2603:10b6:a03:54::32 | SJ2PR17MB6565.namprd17.prod.outlook.com 2603:10b6:a03:4f6::19 | Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) | 2/13/2025 2:40:08 PM | ✅ |
| 5 | 47 seconds | BY5PR17MB3063.namprd17.prod.outlook.com fe80::bf8c:c1de:31b1:4af5 | BY5PR17MB3063.namprd17.prod.outlook.com fe80::bf8c:c1de:31b1:4af5 | mapi | 2/13/2025 2:40:55 PM | ❌ |
Additionally, I would think if the email was fake, they wouldn’t include a legit link to the M365 Admin billing site.
Here is what I believe is going on:
- Scammer sets up junk tenant with the scam text tenant brand info
- Distribution list is created with target email addresses
- DL is used as the billing contact email
- Scammer signs up for trial and/or service (not sure of this part in that when I looked up Dynamics 365 Sales Enterprise Edition, it’s $120 USD /month)
- Email is blasted to all the targets via the DL
Anyway, I thought it was worth a share as this seems like a new twist on using Microsoft tools to try and scam people.
In the meantime, I’ll be trying to poke at Microsoft people to take down the smithkrause domain.